Attackers using Google ads for Ransomware attacks
Attackers using Google ads for ransomware attacks
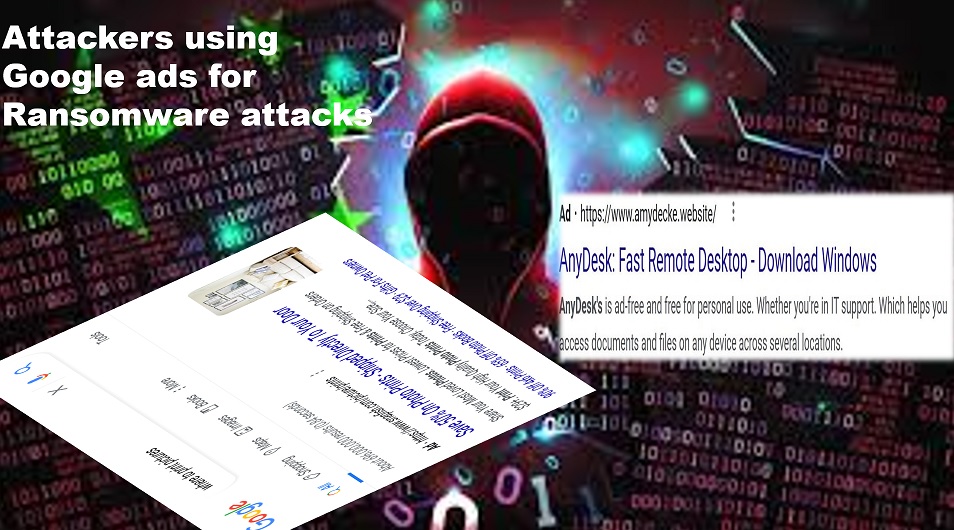
Did you know? Attackers can weaponize Google Ads to target a brand and its customers? Anyone can buy and run ads on Google Search for any set of keywords. All they need to do is pick and keyword and pay for it to be on top of the results page. Scammers do the same. They buy and run ads that show up on top of Google results when a customer/ user searches for a specific brand-related keyword.
When clicked, these ads redirect users to phishing or fraudulent web pages. Some of these websites redirect to phishing pages of the target brand and others might redirect users to elaborate scams like asking them to call a fake customer support number.
These phishing pages trick users into giving up confidential information such as their login credentials, account details, and Personal Identifiable Information (PII). The fake customer support webpages ask users to call a fake customer support number and carry out their scam.
Scammers use this collected information to hijack accounts, drain crypto wallets and use the Personal Identifiable Information to build more data points on their future victims.
In February 2022, Mandiant discovered a malware distribution campaign using SEO poisoning to rank sites pretending to be popular software in search results.
If a user installed the software offered from these pages, it would execute a new malware downloader called BatLoader, which launches a multi-stage infection process that ultimately provides the threat actors with initial access to the victims’ networks.
Later that year, Microsoft reported that the threat actors behind BatLoader, tracked as DEV-0569, had begun to use Google ads to promote their malicious sites. Even worse, Microsoft said that these infections ultimately led to the deployment of Royal Ransomware on breached networks.
“Recent activity from the threat actor that Microsoft tracks as DEV-0569, known to distribute various payloads, has led to the deployment of the Royal ransomware, which first emerged in September 2022 and is being distributed by multiple threat actors,” warned Microsoft in their report.
Attackers are using Google ads to breach your network
Dr Zakir Hussain, vCISO & Security Advisor said that the large number of malicious Google ads being shown in search results is becoming a massive problem for both consumers and the enterprise. With these campaigns being used to gain initial access to corporate networks, they can lead to various attacks, such as data theft, ransomware, and even destructive attacks to disrupt a company’s operations
From Google ads to ransomware attacks
In 2022, Mandiant discovered a malware distribution campaign using SEO poisoning to rank sites pretending to be popular software in search results.
If a user installed the software offered from these pages, it would execute a new malware downloader called BatLoader, which launches a multi-stage infection process that ultimately provides the threat actors with initial access to the victims’ networks.
Later that year, Microsoft reported that the threat actors behind BatLoader, tracked as DEV-0569, had begun to use Google ads to promote their malicious sites. Even worse, Microsoft said that these infections ultimately led to the deployment of Royal Ransomware on breached networks.
“Recent activity from the threat actor that Microsoft tracks as DEV-0569, known to distribute various payloads, has led to the deployment of the Royal ransomware, which first emerged in September 2022 and is being distributed by multiple threat actors,” warned Microsoft in their report.
Researchers believe that DEV-0569 is an initial access broker that uses its malware distribution system to breach corporate networks. They use this access in their own attacks or sell it to other malicious actors, such as the Royal ransomware gang.
January 21st, 2023, when CronUp researcher Germán Fernández noted that recent Google ads promoting popular software led to malicious sites utilizing infrastructure operated by the DEV-0569 threat actors.
While malicious installers in this campaign no longer use BatLoader, like the previous campaigns seen by Microsoft, they install an information-stealer (RedLine Stealer) and then a malware downloader (Gozi/Ursnif).
In the current campaign, RedLine is used to steal data, such as passwords, cookies, and cryptocurrency wallets, while Gozi/Ursnif is used to download further malware.
Fernández told that he linked these new campaigns to DEV-0569 as they were using the same bitbucket repository and the ads-check[.]com URL used in the reported November/December 2022 campaigns.
Fernández did not wait long enough to see if Cobalt Strike and Royal Ransomware would be installed. However, he told that he believed the hackers would eventually use the Gozi infection to drop Cobalt Strike as BatLoader did in previous campaigns.
Fernández also accessed DEV-0569’s web panel used to track their malware distribution campaign and shared screenshots on Twitter. These screenshots showed the legitimate programs being impersonated and the numerous victims worldwide that were infected daily.
When asked how many people were infected by this campaign based on the web panel statistics, he said it was only possible to estimate the number.
“They clean the panel data every campaign day, but there is a data that could give us an idea, it is the correlative ID of the records (it could be an estimated value for the number of victims of this panel, in this case the last value of today is 63576),” Fernández told
Campaign linked to CLOP ransomware
To make matters worse, Fernández discovered that a different but similar Google ads campaign was using infrastructure previously used by a threat group tracked as TA505, known to distribute the CLOP ransomware.
In this Google ads campaign, the threat actors distribute malware through websites pretending to be popular software, such as AnyDesk, Slack, Microsoft Teams, TeamViewer, LibreOffice, Adobe, and, strangely, websites for W-9 IRS forms.
When the malware from this campaign is installed, it will run a PowerShell script that downloads and executes a DLL from the website download-cdn[.]com, which TA505 previously used